VDI: flexVDI with user authentication
Finally, let's create a new VDI configuration in which users have their own list of desktop policies, instead of associating it to the terminal.
Previous requirements
In order to perform this configuration, it is necessary to have a directory service in place; e.g. an LDAP server, Microsoft Active Directory or similar product. Installation and configuration of the server is beyond the scope of this guide. Check with your directory service administrator the right values to use to authenticate users in your directory service. You will also need the credentials of a user that is able to make queries on the branch where users are stored.
Creating Terminal Policy
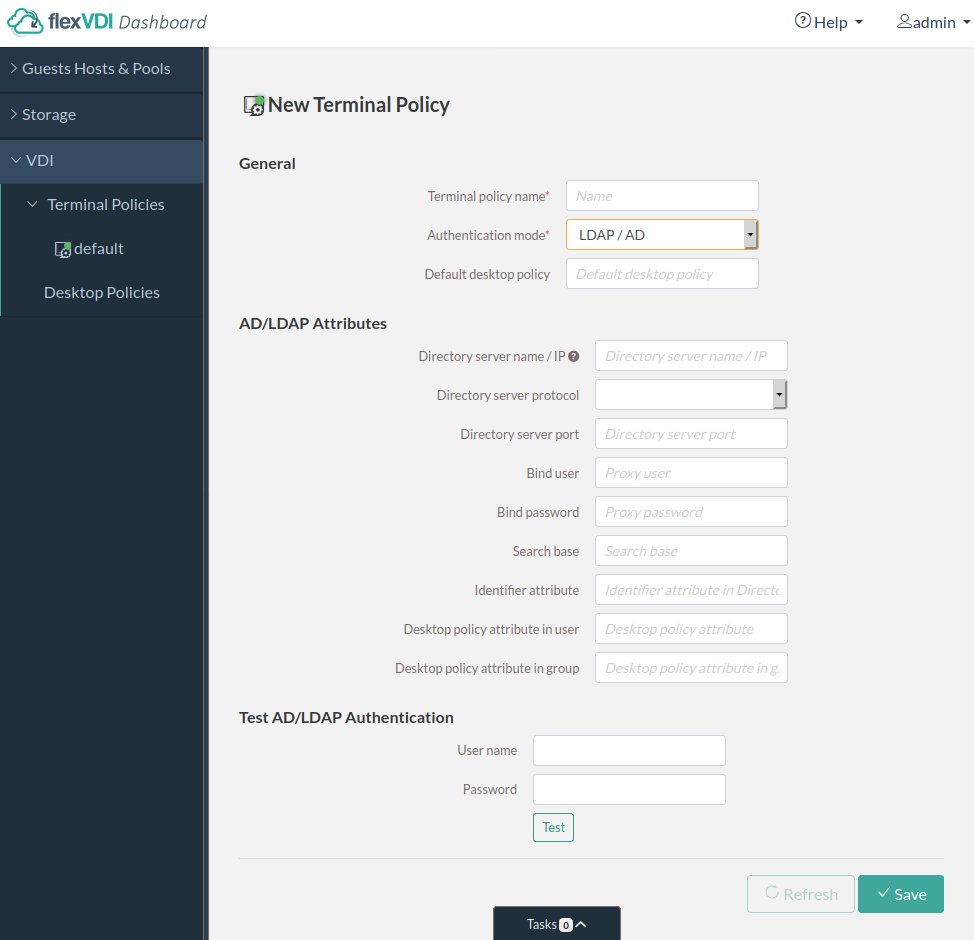
In flexVDI Dashboard, open the VDI section in the tree view and select "Terminal Policies". Then click on the "New Terminal Policy" button. The New Terminal Policy form will be shown:
Enter a name for the new policy and select the "active_directory" authentication mode. New form fields will appear, as shown in the figure. Fill in these fields with the information needed to query the directory server:
- Directory server IP: Name or IP address of the directory server.
- Directory server protocol: LDAP for plaintext, or LDAPS for using ldap over TLS (available since flexVDI Manager 3.1.4). For using LDAPS, you will probably need to add your CA/server certificate to the flexVDI Manager trust store as described at Authenticating users with LDAPS.
- Directory server port: TCP port of the directory server. Usually, it is 389 for LDAP, and 636 for LDAPS.
- Bind user: User to bind to the directory server. It must be able to make queries on the branch where users are stored. If the Authentication server is an Active Directory, the "Proxy user" may also be composed like "NetBIOS Domain Name"\"User Name" or "User Name"@"Domain FQDN". E.g. "MYCOMPANY\Administrator" or "Administrator@mycompany.com".
- Bind password: Password for the bind user.
- Search base: Branch of the directory tree where users are searched. Queries are made in subtree mode. E.g. "cn=Users,dc=companyname,DC=com"
- Identifier attribute: Attribute of user entries that identify them, e.g. cn, sAMAccountName, uid, email, etc.
- Desktop policy attribute in user: Attribute of user entries that stores the desktop policies for each user. You can write a comma-separated list of Desktop Policy names. To simplify user management, flexVDI recommends using an attribute that already exists in your directory schema but is not used. For instance, in an Active Directory, the "info" attribute is hardly ever used and is easily visible and editable with the "AD Users and Computers" tool (it is labeled "Notes").
- Desktop policy attribute in group: The same, but for group entries. All users in a group are assigned to a Desktop Policy in this way.
Read more on configuring a Terminal Policy in the VDI section of the Administration Guide.
You have now set up your "Terminal Policy" with user authentication. Now you must assign the terminals from which authenticated users will connect to this Terminal Policy, as shown in VDI: flexVDI in kiosk mode under the "Assigning a terminal to a terminal policy" header. Also, populate the user entries in your directory with a Desktop Policy name in the desktop policy attribute you selected, so that those users can log in to a desktop.
Accessing the desktop with flexVDI Client
To connect to this new authenticated Terminal Policy, use the flexVDI Client that was installed and configured in the previous page VDI: flexVDI in kiosk mode. flexVDI Client will show a screen like this:
Enter your credentials, and click on login. If you have been assigned only one Desktop Policy, as in the example we have followed so far, flexVDI Client will directly connect to your desktop. If you have been assigned several Desktop Policies, the following is shown so that you can select one of them:
Click on "connect" and the flexVDI Client will show the console of the selected desktop.